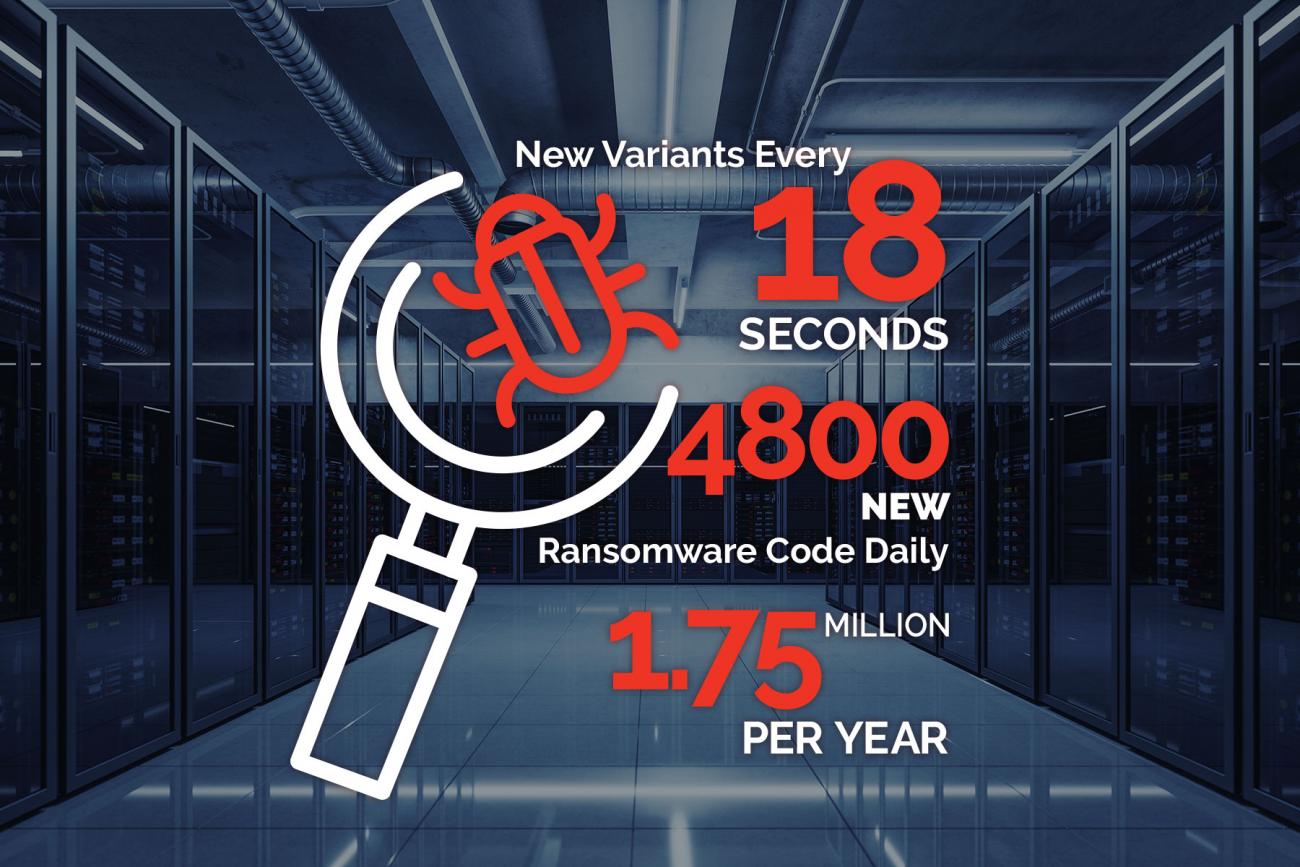
Ransomware is insidious. It is constantly evolving with new variants appearing literally every 18 seconds. That’s 4800 new ransomware code every single day or more than 1.75 million per year. This is a multi-billion USD business. It’s organized criminality and frequently state sponsored. The profits to cybercriminals are compelling.
Authorities continue to advise the best response to a ransomware attack is a good backup and NOT to pay the ransom. It’s good advice that is frequently ignored. The cybercriminals’ price their ransom to make it attractive to pay the nuisance cost versus the time and cost required to recover. Unfortunately, there are consequences for paying the ransom.
- The cybercriminal may or may not decrypt all the data. It’s more likely that they will return access to a large percentage of the data, just not all of it. They will then demand an additional ransom for the rest of the data.
- The cybercriminals now know that the organization is now a known “payer”. They will kidnap the data again or make it known to associates so they can kidnap the data again, many times over.
The cybercriminals also know the best way to force a ransom and ensure their revenue stream, is to make the backups disappear or become ineffective. The best way to make them disappear is by deleting the backups via stolen credentials or via the data protection software published API. Should that fail they will use a Trojan Horse strategy of infect and wait to detonate. This enables the data protection software to back up the infections. When the ransomware finally detonates, recovering from the backups re-infects and re-encrypts the primary data. This is known as an “Attack-Loop”.
What does this have to do with Remote monitoring and management (RMM)? That requires a brief explanation of what RMM is, what it does, and how ransomware is exploiting it.
RMM software helps managed IT service providers (MSPs) remotely and proactively monitor client endpoints, networks and computers. It was historically called remote IT management. Deploying RMM requires an agent installed on client servers, hypervisors, workstations, networking devices, laptops, and other mobile endpoints. The agents continuously report device health information and status back to the MSP providing client insights. For the MSP, it keeps client on-prem machines up-to-date while proactively dealing with problems and issues, often before the client is aware there is one. The RMM issues tickets or alerts to the MSP when it detects a problem classifying them based on severity, problem type, criticality, etc. This is why RMM has become so popular among MSPs.
The main purpose and tasks of RMM have been in summary:
- Monitor the ongoing health and performance of MSP client’s software, server machines (physical/virtual), hypervisors, and networks.
- Keep track historically.
- Initiate alerts and tickets when problems are detected.
- Provide MSPs with actionable information on SLAs, problems, root cause analysis, and paths to correct.
- Monitor all MSP clients and endpoints simultaneously.
- Allows remote admin access to all monitored machines.
- Automate scheduled maintenance tasks.
RMMs appear to be extremely helpful (and profitable) tool for MSPs. And RMMs have not stopped evolving. Many have tightly integrated backup software today so the MSP can provide backup as a service (BaaS) and DR as a service (DRaaS) as part of their software platform. Several RMM vendors purchased backup software to specifically integrate with their RMMs. Single sign-in and more services in a single UI. All good for the MSP? Maybe not. This is where ransomware has come into the picture. Remember, the cybercriminals want to eliminate or at least mitigate the ability of the backups to stop their attack. This has made RMMs with integrated backups incredibly attractive to their potential revenues.
The next blog will cover the RMM ransomware attack vector; how their frequency is increasing; and what MSPs can do to dramatically reduce their exposure.