
Enterprise Backup and Recovery with Advanced Ransomware Protection
Asigra Tigris combines industry-leading backup and recovery with advanced security designed to protect your backups from today’s new breed of cyber attacks. Maximize your odds of data recovery with a single, integrated solution that is easy to manage and proactively protects your data like no other solution available today.
Tigris is delivered as-a-service through Asigra’s global network of MSP partners.


Fast and Comprehensive Backup and Recovery
-
Back up and recover data from multiple workloads, including SaaS, files, databases and more.
-
Automate full or incremental backup schedules.
-
Full or granular recovery.
-
Backup integrity features like Restore Validation and Autonomic Healing ensure data can be recovered quickly, reliably, and without loss or corruption.

Reliable Ransomware Protection
-
Asigra’s integrated security framework protects your backups against ransomware that circumvent traditional air gapped and immutable solutions.
-
NIST-FIPS 140-certified AES 256 bit encryption for in-flight and at-rest data ensures your data is secure.
-
MFA and new MPA (Multiperson Approval) prevent unauthorized or accidental actions that may result in data loss.

Easy Deployment
and Management
-
Agentless architecture makes deployment fast and easy.
-
Reduced costs with minimal infrastructure requirements.
-
Optimize on/off-premise or cloud storage to suit your specific needs.
-
Asigra's Web-based management console lets you manage your backup environment on a global or tenant level.
Multiperson Approval (MPA)
Ransomware isn’t the only threat to your backup data. Credential theft methods allow cybercriminals to gain access to your backups and attempt to delete them or modify your retention period in advance of a ransomware attack. Without your backups, you have no way of recovering your data.
New in Tigris 14.2
MPA is an industry-first feature in backup security and works together with MFA (Multifactor Authentication) to thwart unauthorized actions against your data as a result of credentials theft.
Administrators configure accounts to require additional managers to approve a potentially destructive action that can result in data loss. When a user attempts to perform a destructive task, one or more users are notified and must approve the request within 30 minutes.
Administrators can customize thresholds and settings to specify how many additional approvals are required and which actions require the approvals.
Read More About MPA and Credentials Theft
Learn about the basics of credential theft prevention and backups.

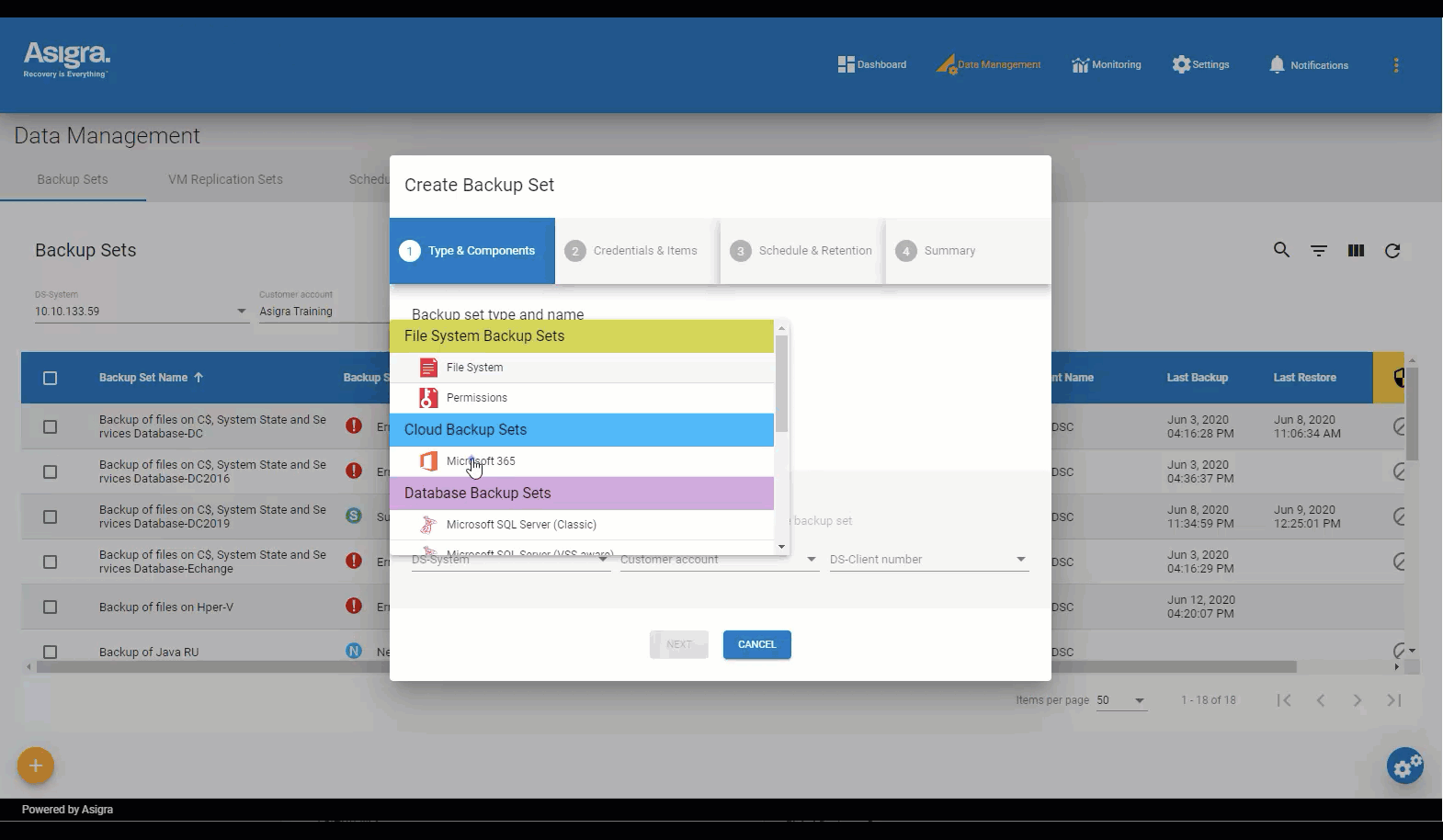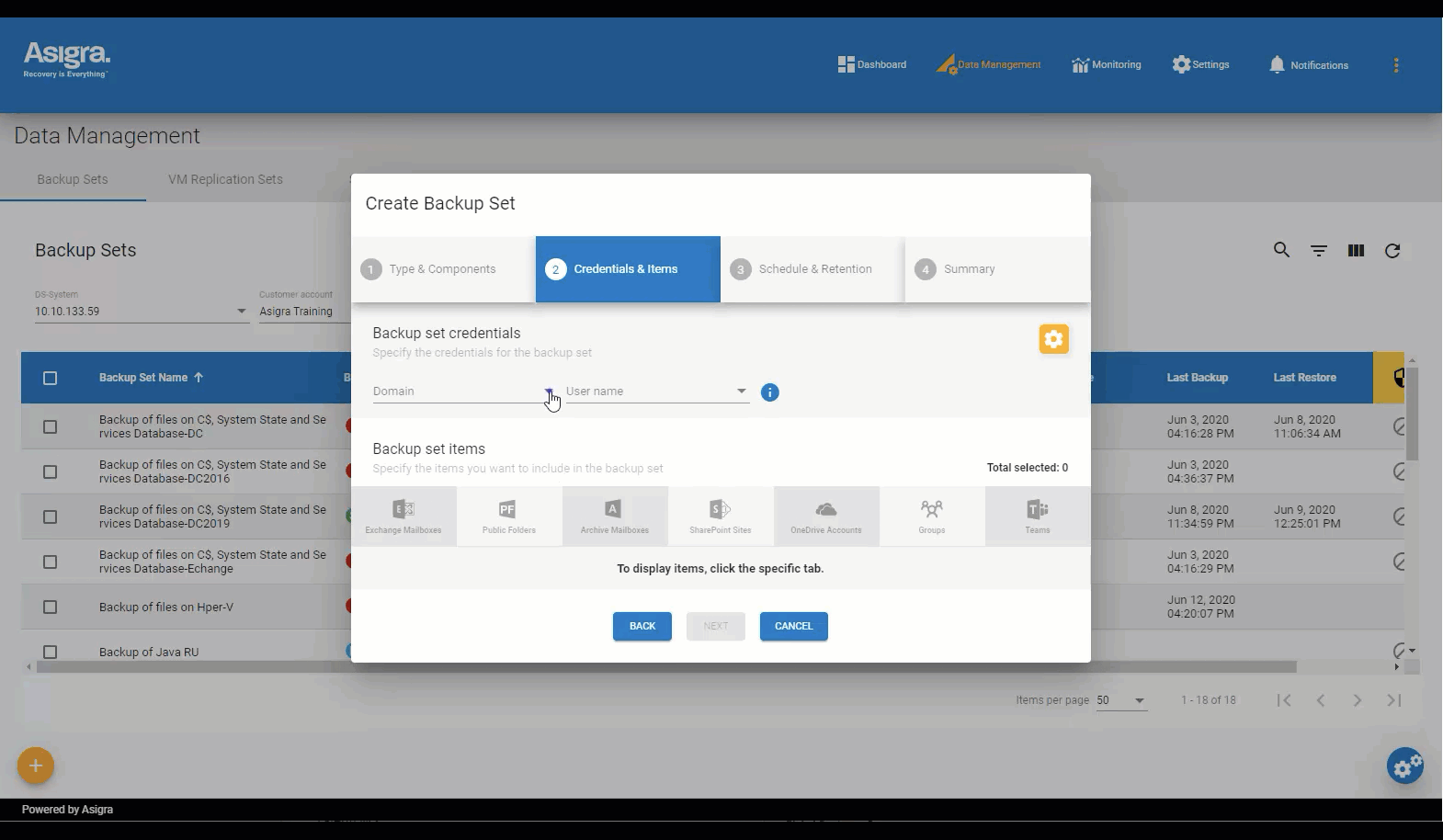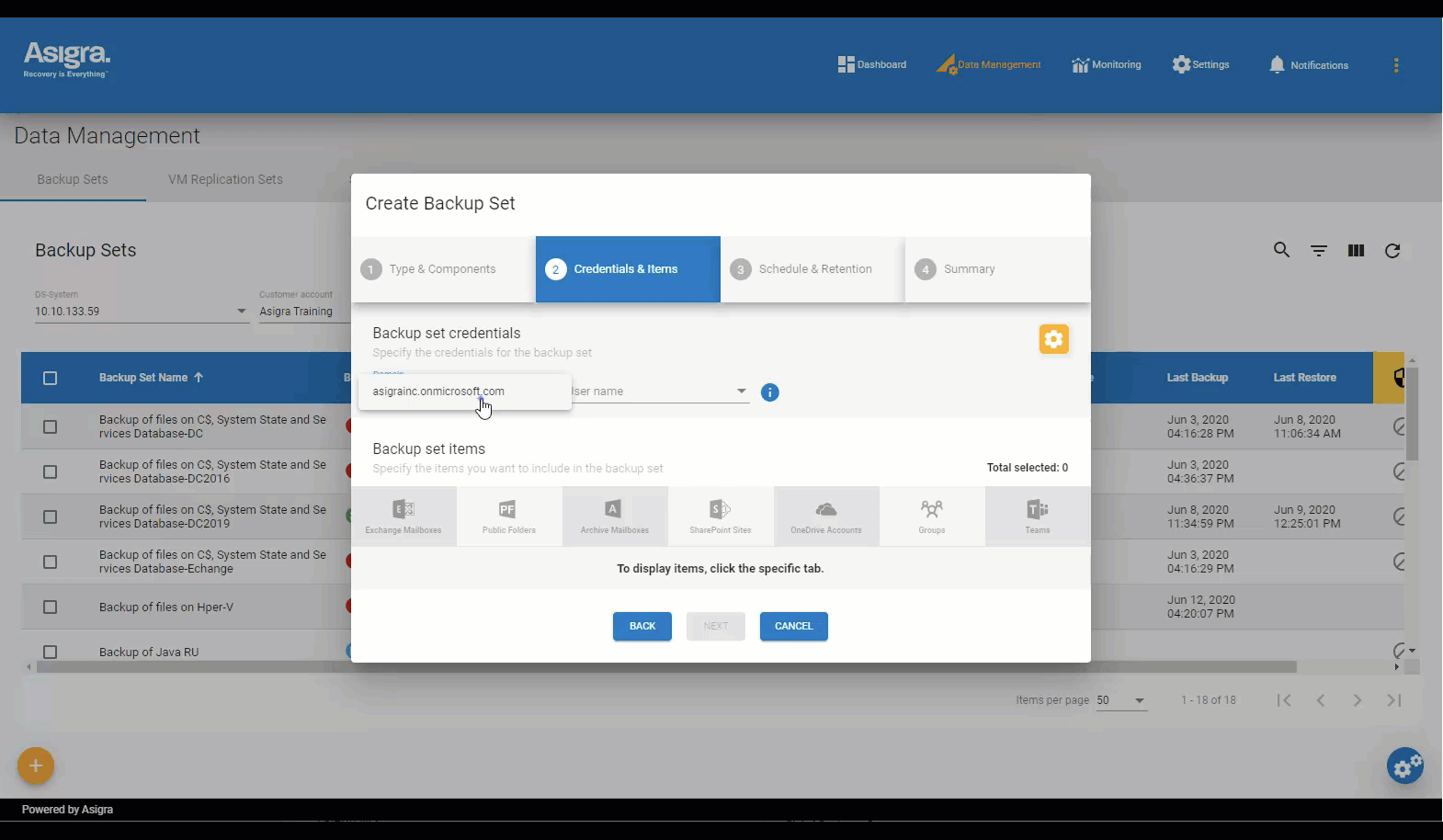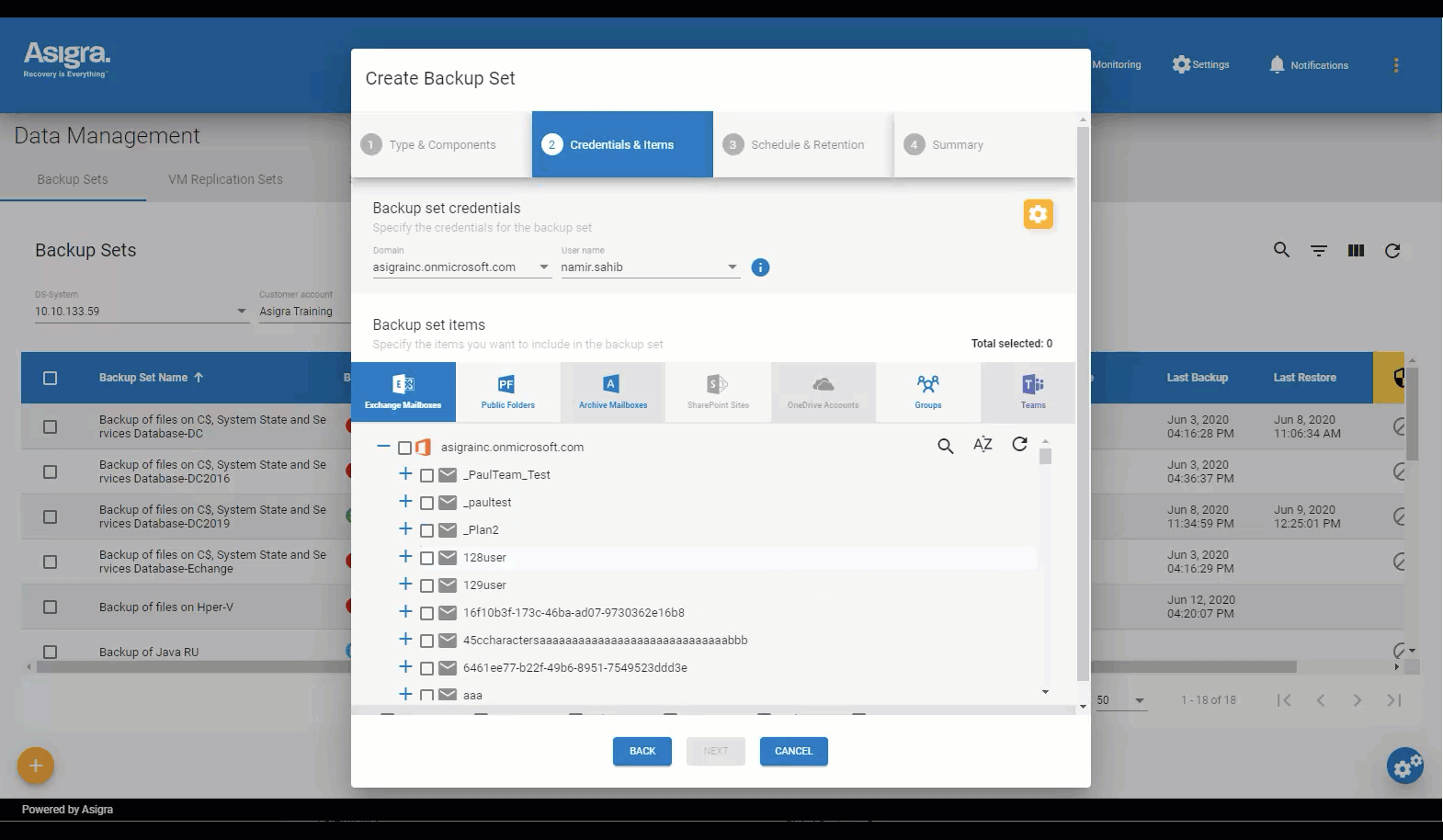
Asigra Management Console
A simplified way to manage your Tigris backup environment
The Asigra Management Console is a Web-based command center that gives you instant access and visibility to your entire Tigris backup and recovery environment.
The console lets you schedule and initiate backup and recovery sessions easily for Windows, macOS and Linux file systems, Microsoft 365, VMware Center Servers, and more.
Monitoring is also easy thanks to an intuitive graphical dashboard, with the ability to generate multiple reports and view event, activity, and audit logs.
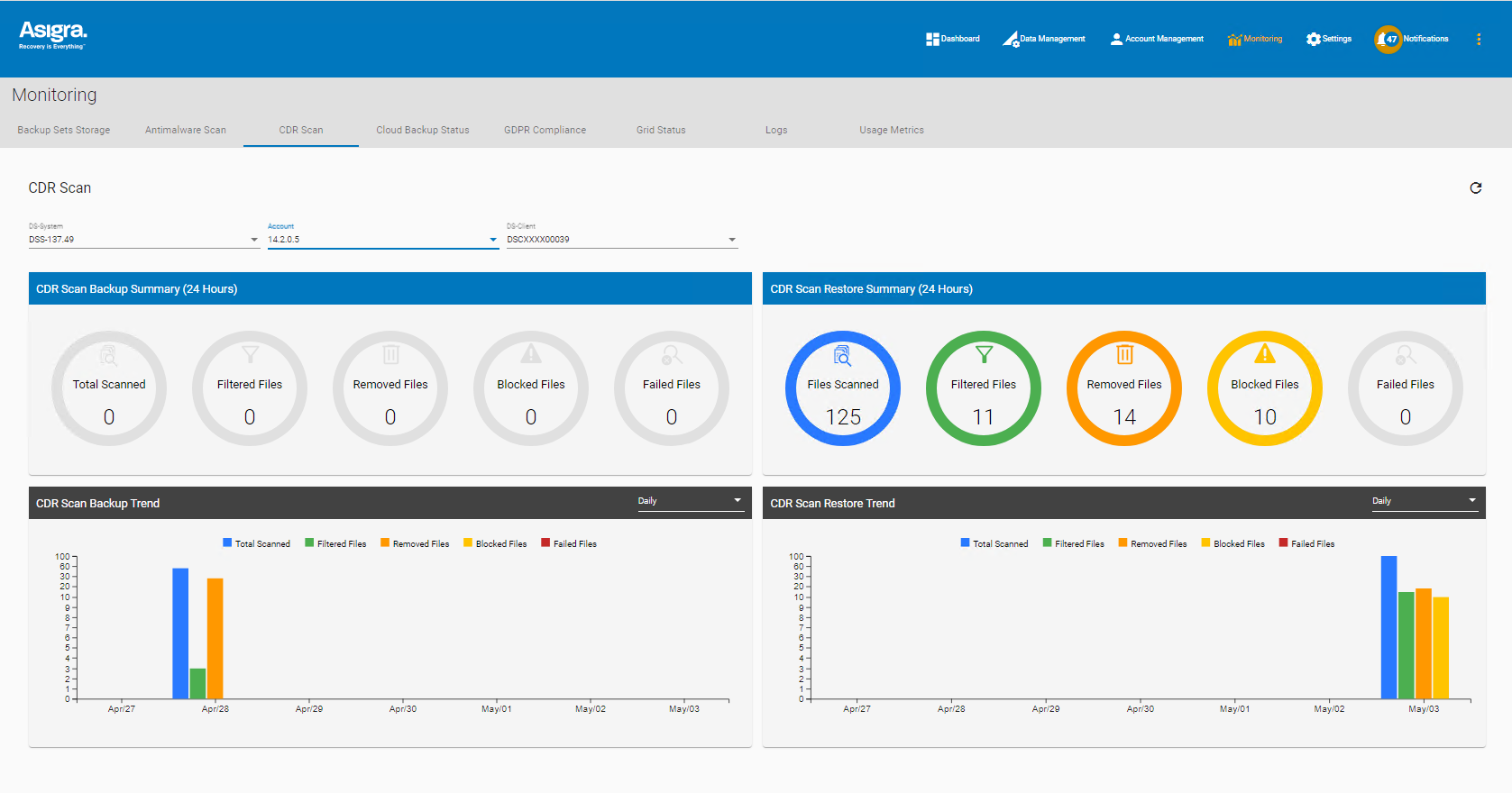
Content Disarm and Reconstruction (CDR)
Attackers will also make use of malicious code embedded deeply within multi-layered files that avoid antimalware detection.
Asigra's advanced CDR security attacks this problem by taking multilayered files, like Microsoft Office or PDF files, and first deconstructing them into their individual layers, and then scanning each layer for any foreign script, macro, or other code that may represent a threat.
Based on your predefined policies, Tigris will filter, block, or remove potentially dangerous content. You can remove the file completely during recovery, strip out the suspected content from the file, or restore the file unchanged. This ensures that the backed-up files are free from malicious content while still usable after a recovery.
See CDR in Action
Watch our short demo of CDR and Antimalware scanning in action.
Asigra has impressed our team of IT experts, addressing some of the most difficult challenges around backup efficiency, security and compliance.”
|
Physical File Systems (Servers and Client) |
Microsoft Windows (FAT/NTFS), Linux (NFS/SSH), Apple Mac OS X (NFS, APFS) |
|
Virtual Machines |
Microsoft Hyper-V Server, VMware VCenter Server, VMware Cloud Director |
|
Enterprise Applications |
Microsoft Exchange Server, Outlook, SharePoint Server |
|
Cloud Applications (SaaS) |
Microsoft 365, Salesforce, Google Workspace
|
|
Enterprise Databases |
Microsoft SQL Server, Oracle Database, Oracle MySQL, Oracle SBT, IBM DB2, PostgreSQL |
|
VM Replication |
VMware virtual machines may be replicated between two vCenters. Replication sets can contain either individual Virtual Machines or Virtual Machine Folders. |
|
Agentless Endpoint Architecture |
DS-Client coordinates backup and recovery on the local LAN level without the need to install and manage agents on individual endpoints. |
|
Multitenancy Support |
Offer backup as a service to multiple individual clients on a single instance. |
|
Location and Storage Agnostic |
Tigris is storage agnostic and will work with local or cloud-based NAS, SAN or DAS storage appliances and environments
|
|
LAN Storage Discovery |
Analyze the deployment environment to optimize the cost and time of backing up data. Identify redundant and stale data, isolate storage issues, and create reports to help you design suitable backup, recovery, and retention strategies. |
|
Customer Billing and Reporting |
DS-Billing provides a toolkit for managing billing and chargeback, including templates for reporting and invoicing.
|
|
High Availability and Fault Tolerance |
Options for standalone or N+1 deployment to provide fault tolerance and load balancing. |
|
Full and Incremental Backup |
The initial backup is a full backup, after which all other backups are incremental. Users may perform an initial backup via a removable drive when full network transfers are impractical due to limited bandwidth. |
|
Delta Processing |
Analyzes files at the block level for changes, reduces storage requirements and increases backup speed. |
|
Data Deduplication |
Duplicate files are identified, and only one copy is backed up, reducing storage requirements. |
|
Automatic Retry on Connection Interruption |
In the event of a network interruption, the system will attempt reconnection and resume backup based on what files were being processed at the time of the interruption. |
|
Multiple Backup Sets |
Create multiple independent backup sets for the same source system. Include or exclude files and databases by directories or file type. Define the number of retained generations or versions of files that have been backed up. |
|
Backup Lifecycle Management Archiver |
Manage long-term retention policies for backup sets that align with compliance requirements. Move long-term storage sets to separate, lower-cost storage while keeping critical data immediately available for recovery. Move data to s3 compatible storage services. |
|
Scheduling |
Supports calendar-based scheduling for automatically executing backup sets. Define on a daily, weekly, monthly, or at random frequency. |
|
Defined Policies |
Define policies based on multiple factors, including how long files are kept, backup frequency, and more |
|
Monitoring |
Monitor and review backup activities through the DS-User GUI, Management Console, and the DS-NOC web interfaces. Access detailed logs of backup activity, error reports, details of files backed up, license levels, and backup audit trails. Set email alert notifications. |
|
Master Reconstruction |
Reconcile the oldest master copy and accumulated delta backups into a new master copy. |
|
Full or Granular Recovery |
Conduct full, or selective recovery of data. |
|
Incremental Forever |
Optimize backup windows by rebuilding full backups from incremental changes or reverse it and restore files to any point in backup history. |
|
Recoverability Methods |
Select one of four methods to restore data locally, across the network, from a portable disk, or delivered from an alternate disaster recovery location. |
|
Autonomic Healing |
Maximize recoverability by monitoring the integrity of backup data and repairing it automatically if corruption is found. |
|
Restore Validation |
Simulate a recovery in memory to ensure your recovery will succeed when needed. |
|
Encryption |
Backup data is encrypted in flight using AES (128, 192, or 256-bit) encryption algorithm and is always stored encrypted. |
|
Encryption Certifications |
AES – certificate #968 |
|
Access Control |
Role-based access control can be defined for different levels of access for internal and external users. |
|
AntiRansomware Scanning |
Conduct bidirectional antimalware scanning during backup and recovery phases.
|
|
Quarantine and Remediation |
Infected files are encrypted upon backup, so they cannot infect the data repository. Administrators can quarantine infected files in a password-protected zip file or clean the files during the restore phase.
|
|
Content Disarm & Reconstruction (CDR) |
Scan for deeply embedded code or scripts in multi-layered Windows file backups. Action potential threats based on pre-defined policies:
|
|
Multifactor Authentication (MFA) |
Require users to authenticate using time-based one-time passwords (TOTP) when signing into the Management Console or attempting to perform a potentially destructive action that can result in the loss of data.
|
|
Multiperson Approval (MPA) |
Configure user accounts to require multiple people to approve actions that can result in the loss of data. Set thresholds to specify how many approvals are required, and which actions require additional approval.
|
|
Soft Delete |
Two-step deletion process that holds deleted data in a specified location and protects against accidental or malicious data deletions. |
|
Variable Repository Naming |
Thwart attackers who target backup repositories by searching for known backup repository naming conventions. |
|
Management Console |
Gain insights and manage your Tigris backup environment from a centralized web-based management console. |
|
Dashboards and Reporting |
Access Dashboards for status monitoring and alerts, as well as a comprehensive series of reports:
|
|
API Management Integration |
The Management Console supports RESTful APIs that allows for integration into existing web-based management systems. |
|
Administration Delegation |
DS-Operator roles can be defined to establish permissions for different users and groups. |
|
Management Console Logs |
Search and view system Activity logs based on backup set names:
|
-
Physical File Systems (Servers and Client)
Microsoft Windows (FAT/NTFS), Linux (NFS/SSH), Apple Mac OS X (NFS, APFS)
Virtual Machines
Microsoft Hyper-V Server, VMware VCenter Server, VMware Cloud Director
Enterprise Applications
Microsoft Exchange Server, Outlook, SharePoint Server
Cloud Applications (SaaS)
Microsoft 365, Salesforce, Google Workspace
- MS 365 supports autodiscovery to automatically create backup sets for items added to the MS 365 domain.
Enterprise Databases
Microsoft SQL Server, Oracle Database, Oracle MySQL, Oracle SBT, IBM DB2, PostgreSQL
VM Replication
VMware virtual machines may be replicated between two vCenters.
Replication sets can contain either individual Virtual Machines or Virtual Machine Folders.
-
Agentless Endpoint Architecture
DS-Client coordinates backup and recovery on the local LAN level without the need to install and manage agents on individual endpoints.
Multitenancy Support
Offer backup as a service to multiple individual clients on a single instance.
Location and Storage Agnostic
Tigris is storage agnostic and will work with local or cloud-based NAS, SAN or DAS storage appliances and environments
- Supports block-based and file-based protocols.
-
Certified for iXsystems TrueNAS appliance and Zadara’s cloud-based virtual appliance storage solutions.
LAN Storage Discovery
Analyze the deployment environment to optimize the cost and time of backing up data. Identify redundant and stale data, isolate storage issues, and create reports to help you design suitable backup, recovery, and retention strategies.
Customer Billing and Reporting
DS-Billing provides a toolkit for managing billing and chargeback, including templates for reporting and invoicing.
-
Export billing data to your existing billing system in CSV, HTML, and XLS format.
-
Automate report and bill generation.
High Availability and Fault Tolerance
Options for standalone or N+1 deployment to provide fault tolerance and load balancing.
-
Full and Incremental Backup
The initial backup is a full backup, after which all other backups are incremental.
Users may perform an initial backup via a removable drive when full network transfers are impractical due to limited bandwidth.
Delta Processing
Analyzes files at the block level for changes, reduces storage requirements and increases backup speed.
Data Deduplication
Duplicate files are identified, and only one copy is backed up, reducing storage requirements.
Automatic Retry on Connection Interruption
In the event of a network interruption, the system will attempt reconnection and resume backup based on what files were being processed at the time of the interruption.
Multiple Backup Sets
Create multiple independent backup sets for the same source system.
Include or exclude files and databases by directories or file type.
Define the number of retained generations or versions of files that have been backed up.
Backup Lifecycle Management Archiver
Manage long-term retention policies for backup sets that align with compliance requirements.
Move long-term storage sets to separate, lower-cost storage while keeping critical data immediately available for recovery.
Move data to s3 compatible storage services.
Scheduling
Supports calendar-based scheduling for automatically executing backup sets. Define on a daily, weekly, monthly, or at random frequency.
Defined Policies
Define policies based on multiple factors, including how long files are kept, backup frequency, and more
Monitoring
Monitor and review backup activities through the DS-User GUI, Management Console, and the DS-NOC web interfaces. Access detailed logs of backup activity, error reports, details of files backed up, license levels, and backup audit trails.
Set email alert notifications.
Master Reconstruction
Reconcile the oldest master copy and accumulated delta backups into a new master copy.
-
Full or Granular Recovery
Conduct full, or selective recovery of data.
Incremental Forever
Optimize backup windows by rebuilding full backups from incremental changes or reverse it and restore files to any point in backup history.
Recoverability Methods
Select one of four methods to restore data locally, across the network, from a portable disk, or delivered from an alternate disaster recovery location.
Autonomic Healing
Maximize recoverability by monitoring the integrity of backup data and repairing it automatically if corruption is found.
Restore Validation
Simulate a recovery in memory to ensure your recovery will succeed when needed.
-
Encryption
Backup data is encrypted in flight using AES (128, 192, or 256-bit) encryption algorithm and is always stored encrypted.
Windows DS-Client supports TLS 1.3 encryption protocolEncryption Certifications
AES – certificate #968
Random Number Generation – certificate #546
Digital Signature – certificate #938
HMAC – certificate #541
NIST FIPS 140-2Access Control
Role-based access control can be defined for different levels of access for internal and external users.
AntiRansomware Scanning
Conduct bidirectional antimalware scanning during backup and recovery phases.
- Requires Management Console 14.2.0.8 and supports Windows, Linux, or Mac file systems.
Quarantine and Remediation
Infected files are encrypted upon backup, so they cannot infect the data repository. Administrators can quarantine infected files in a password-protected zip file or clean the files during the restore phase.
- Requires Management Console 14.2.0.8 and supports Windows, Linux, or Mac file systems.
Content Disarm & Reconstruction (CDR)
Scan for deeply embedded code or scripts in multi-layered Windows file backups.
Action potential threats based on pre-defined policies:
- Block — Quarantines the entire file if it contains any malicious or non-malicious embedded code
- Remove — Extracts the malicious or non-malicious code and reconstructs the file without the embedded code
- Filter — Extracts the embedded content and performs five levels of analysis to determine whether it is malicious or harmless before either quarantining it or leaving the file unchanged.
- Requires Management Console 14.2.0.8 and supports Windows file systems.
Multifactor Authentication (MFA)
Require users to authenticate using time-based one-time passwords (TOTP) when signing into the Management Console or attempting to perform a potentially destructive action that can result in the loss of data.
- Requires Management Console 14.2.0.8 or later and a six-digit Time-based One-time password (TOTP) generator application such as Google or Microsoft Authenticator app.
Multiperson Approval (MPA)
Configure user accounts to require multiple people to approve actions that can result in the loss of data. Set thresholds to specify how many approvals are required, and which actions require additional approval.
- Requires Management Console 14.2.0.8, Windows DS-Client 14.2.0.8 or Linux DS-Client 14.2.0.6, DS-System 14.2.0.6, and DS-Operator 14.2.0.6 or later.
Soft Delete
Two-step deletion process that holds deleted data in a specified location and protects against accidental or malicious data deletions.
Variable Repository Naming
Thwart attackers who target backup repositories by searching for known backup repository naming conventions.
-
Management Console
Gain insights and manage your Tigris backup environment from a centralized web-based management console.
Run backups and recovery activities for all source data through a unified interface.Dashboards and Reporting
Access Dashboards for status monitoring and alerts, as well as a comprehensive series of reports:
- Backup Sets Storage
- Cloud Backup Status
- Antimalware Scan
- CDR Scans
- GDPR Compliance
API Management Integration
The Management Console supports RESTful APIs that allows for integration into existing web-based management systems.
Administration Delegation
DS-Operator roles can be defined to establish permissions for different users and groups.
Management Console and DS-User access can be set up with a variety of permissions for functions including backup, restore, delete, modify, etc.Management Console Logs
Search and view system Activity logs based on backup set names:
- Activity
- Event
- Audit





