Security-First Approach to Backup
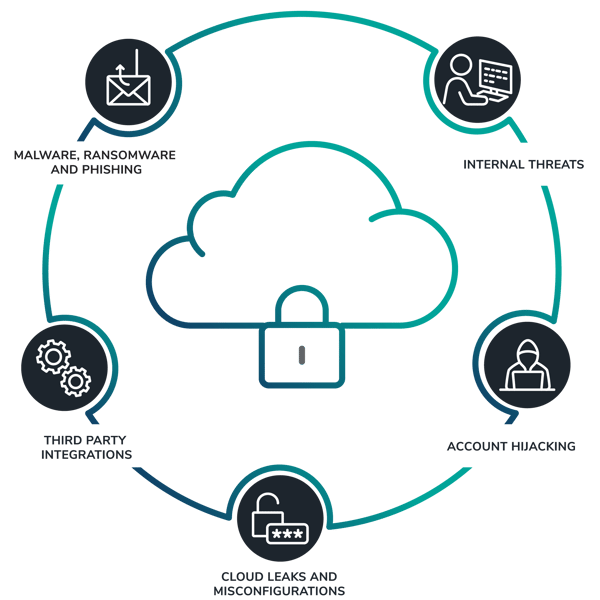
Creating regular backups is critical to protecting valuable business data from potential disasters that lead to loss or destruction, but it's only part of the solution.
Modern cybercriminals now target backup repositories themselves because they know that if you're unable to recover your information, you're more likely to agree to their demands, like a ransomware payout, for example.
In addition, not all threats are external. Some are the result of internal accidents or user errors.
The end result is the same: SaaS data backups are at risk. You need a proactive approach to protecting backup repositories from malicious or accidental compromise.